Monitoring and Reporting Exchange Admin Audit Logs
Use PowerShell to Monitor and Report Exchange Admin Audit Logs
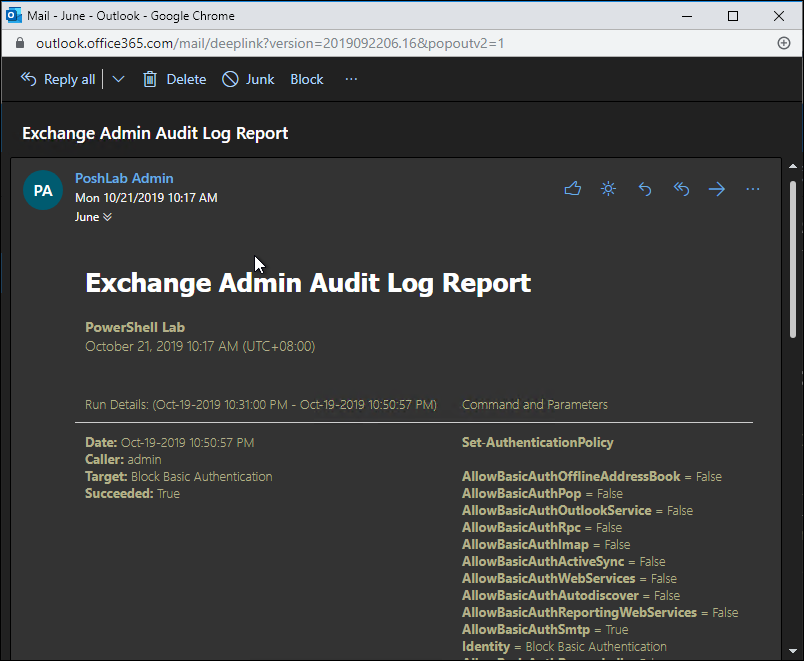
Monitoring and Reporting Exchange Admin Audit Logs
ExCmdReport Module
This module uses the Search-AdminAuditLog Exchange CmdLet under the hood. This can be used to retrieve Exchange Admin Audit Logs from Exchange Online or Exchange Server On-Premises. It uses pagination automatically so that it can retrieve any number of results.
The output can be saved as a pre-formatted HTML file with the option to send as email to specified recipients.
Requirements
This module was tested with the following.
- Windows PowerShell 5.1
- Exchange Online (Office 365)
- Exchange Server 2016 (On-Premises).
- May work with Exchange 2013 and Exchange 2019.
- Remote PowerShell session must be established.
- Exchange Admin Audit Logging must be enabled. Otherwise, there will be no data to return.
How to Install
Option 1: Install from PSGallery
1
Install-Module ExCmdReport -Scope AllUsers
Option 2: Download from GitHub and install manually
Use this if you can’t install the module from PSGallery.
- Download or clone from the GitHub Repository.
- Extract the zip and run
.\InstallMe.ps1in PowerShell.
Usage Examples
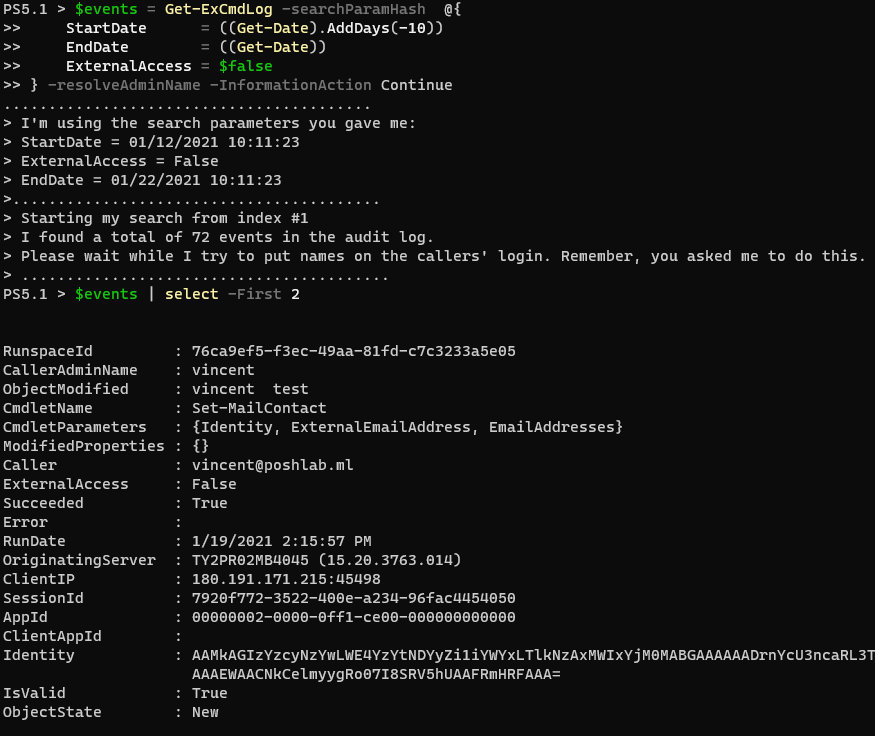
Example 1: Get Admin Audit Log Entries
1
2
3
4
5
6
<# Get ALL log entries #>
Get-ExCmdLog -searchParamHash @{
StartDate = '10/01/2019'
EndDate = '10/10/2019'
ExternalAccess = $false
} -Verbose -resolveAdminName
Example 2: Get Admin Audit Log Entries and Send Email Report
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
<# Build report parameters #>
$report = @{
SendEmail = $true
From = 'admin@domain.com'
To = 'user1@domain.com','user2@domain.com'
smtpServer = 'smtp.office365.com'
port = 587
UseSSL = $true
Credential = (Get-Credential)
TruncateLongValue = 50
}
<# Get Audit Logs and then send #>
Get-ExCmdLog -searchParamHash @{
StartDate = '10/01/2019'
EndDate = '10/10/2019'
ExternalAccess = $false
} -Verbose -resolveAdminName | Write-ExCmdReport @report -Verbose
Functions
There are four functions included in this version. For details, follow the links below.
This post is licensed under CC BY 4.0 by the author.